Three days after connecting to the hotel Wi-Fi, my crypto wallet was emptied
Jan 10, 2026 11:51:52


Original Author: The Smart Ape
Original Compilation: Shenchao TechFlow
A few days ago, I went on a year-end holiday with my family at a very nice hotel. One day after leaving the hotel, my wallet was completely emptied. I was baffled because I had neither clicked on any phishing links nor signed any malicious transactions.
After hours of investigation and consulting experts, I finally understood the truth. It all happened because of the hotel’s Wi-Fi network, a brief phone call, and a series of foolish mistakes.
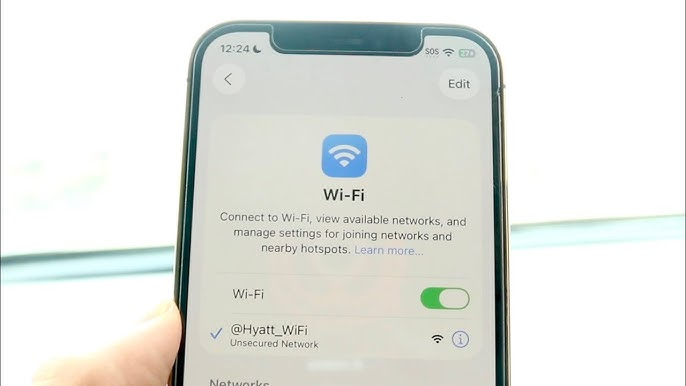
Like most cryptocurrency enthusiasts, I brought my laptop with me, thinking I could squeeze in some work while spending time with my family. My wife repeatedly insisted that I shouldn’t work during these three days, and I really should have listened to her.
Like other guests, I connected to the hotel’s Wi-Fi network. This network didn’t require a password; you just had to log in through a captive portal.

I worked in the hotel as usual, without taking any risky actions: no creating new wallets, no clicking on strange links, and no visiting suspicious decentralized applications (dApps). I just checked X (Twitter), my balance, Discord, and Telegram.
At one point, I received a call from a friend in the crypto space, and we talked about market trends, Bitcoin, and related topics. What I didn’t know was that someone nearby was eavesdropping on our conversation and realized I was involved in cryptocurrency. This was my first mistake. The person learned from our conversation that I was using a Phantom wallet and that I was a significant holder.
This made me a target.
On a public Wi-Fi network, all devices share the same network, and in reality, the visibility between devices is higher than you might think. There are almost no real protections between users, which opens the door for a "Man-in-the-Middle Attack." The attacker acts like a middleman, quietly inserting themselves between you and the internet, just like someone reading and altering the contents of your letters before they are delivered.
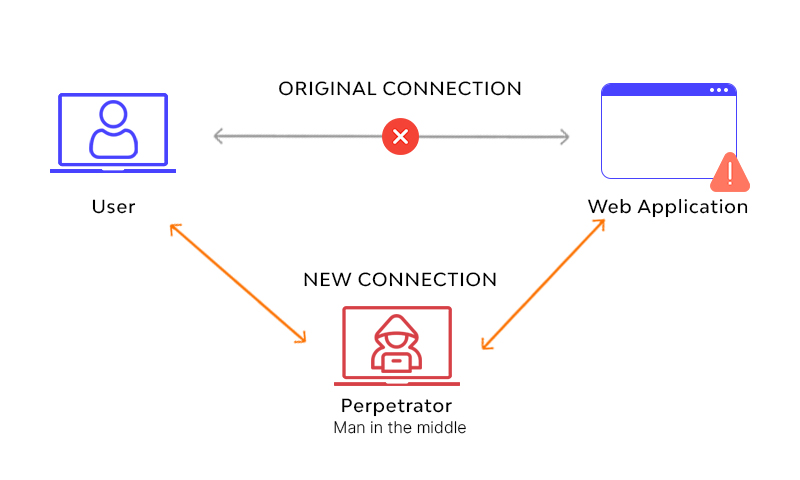
When I was browsing the web on the hotel Wi-Fi, one website appeared to load normally, but in reality, it had additional malicious code injected behind the scenes. I didn’t notice anything unusual at the time. If I had installed some security tools, I could have detected these issues, but unfortunately, I didn’t.
Typically, a website might request your wallet to sign certain operations. The Phantom wallet would pop up a window where you could choose to approve or deny. Generally, you would feel safe signing because you trust the website and browser. However, I shouldn’t have done that that day.
While I was performing a token swap on the @JupiterExchange platform, the malicious code triggered a wallet request that replaced my normal swap operation. I could have detected this as a malicious request by carefully checking the transaction details, but since I was already swapping on the Jupiter platform, I had no suspicions at all.
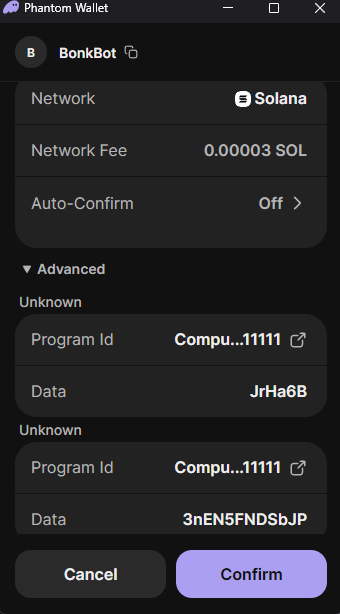
That day, I didn’t sign any transactions to transfer funds; instead, I signed an authorization. This was precisely why my assets were stolen days later.
The malicious code didn’t directly ask me to send SOL (Solana) because that would have been too obvious. Instead, it requested me to "authorize access," "approve account," or "confirm session." In simple terms, I actually gave another address permission to operate on my behalf.
I approved it because I mistakenly thought it was related to my actions on Jupiter. At the time, the information popped up by the Phantom wallet looked very technical, didn’t display any amounts, and didn’t prompt for an immediate transfer.
And that was everything the attacker needed. He patiently waited until I left the hotel to act. He transferred my SOL, withdrew my tokens, and moved my NFTs to another address.
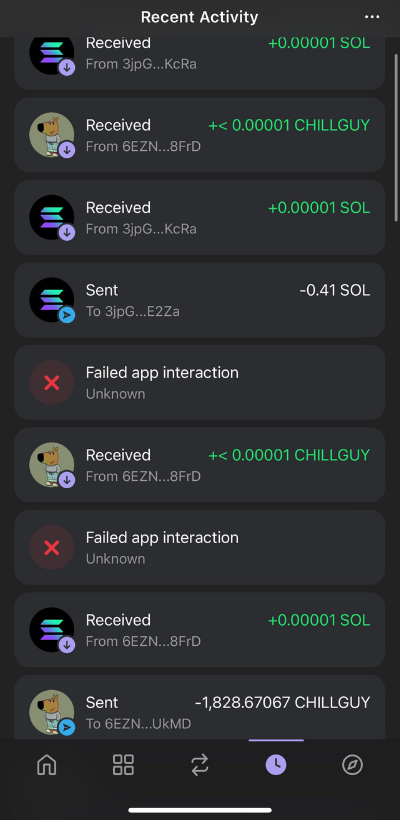
I never thought such a thing would happen to me. Fortunately, this wasn’t my main wallet, but rather a hot wallet used for specific operations, not for holding assets long-term. But even so, I made many mistakes, and I believe I bear primary responsibility for this.
First, I should never have connected to the hotel’s public Wi-Fi. I should have used my phone’s hotspot to go online.
My second mistake was discussing cryptocurrency in the hotel’s public areas, allowing many people to potentially overhear our conversation. My father once advised me never to let others know that I was involved in cryptocurrency. I was lucky this time; some people have even faced kidnapping or worse due to their crypto assets.
Another mistake was approving the wallet request without fully paying attention. Because I was confident that the request came from Jupiter, I didn’t analyze it carefully. In fact, every wallet request should be scrutinized, even on trusted applications. Requests can be intercepted and may not actually come from the application you think.
In the end, I lost about $5,000 from a secondary wallet. While this isn’t the worst-case scenario, it’s still very frustrating.
Latest News
ChainCatcher
Jan 15, 2026 01:22:37
ChainCatcher
Jan 15, 2026 01:19:40
ChainCatcher
Jan 15, 2026 01:17:40
ChainCatcher
Jan 15, 2026 01:16:41
ChainCatcher
Jan 15, 2026 01:14:38























